10 Factors Warehouse Managers Should Consider for Goods-to-Person Fulfilment
In this article, let's dive deeper into how it works and what factors you should consider if you are thinking to switch to using the Goods-to-Person fulfillment model.
Access Control Key to Cybersecurity in B2B eCommerce
Using Access Control Lists (ACLs) to establish rules that grant or deny access to different data types includes sensitive data. Every user in an application has a role, and every role has a set of permissions configured to perform or restrict actions to entities and system capabilities.
What Security Privileges Should We Give to AI?
In a survey, some 80% of telecommunications executives stated they believe their organization cannot respond appropriately to cyberattacks without AI. What's more, 69% of all senior executives agree they would not be able to respond without AI on their side.
Could Your Robot Be Spying on You? - Cybersecurity Tips for Manufacturers Employing Robotics
Whether it is smart phone manufacturing, car-making or the food and beverage sector, factories around the world are already equipped with robots and other automated technologies. So how much of a threat is the possibility of these robots being hacked?
Ways to Optimize Manufacturing Cybersecurity
Manufacturing facilities are at an increasingly high risk of cyberattacks, especially as they feature more connected, advanced machines that play vital roles in operations.
Surviving a Global Cyberattack - Company Culture Plays a Pivotal Role
Pilz was hit with a ransomware cyberattack on October 13, 2019. In the following article, written by Mike Beerman, CEO, Pilz USA, discusses how Pilz not only survived the attack, but is coming back stronger than ever.
Robot Network Security
RAD solutions are used in a variety of markets for critical infrastructure like corporate headquarters, healthcare campuses, higher education campuses, event venues and government facilities.
Securing The Robots
There is no magic bullet for robot security. They are simply devices executing code, which are just as likely to be compromised as any other device in an organisation.
Report: Cyberattacks on Industrial Robots
Trend Micro recently released the first in-depth, hands-on research that demonstrates the extent to which industrial robots can be compromised.
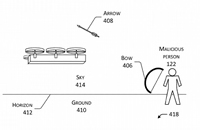
Amazon patents system to defend drones against hackers, jammers … and arrows
Alan Boyle for GeekWire: If there are any Robin Hoods out there who are thinking about shooting down drones while they’re making deliveries, Amazon has a patented plan to stop you.
The patent, filed in 2014 but published just last week, lays out countermeasures for potential threats ranging from computer hacking to lightning flashes to bows and arrows.
If nothing else, the 33-page application illustrates how many things could possibly go wrong with an autonomous navigation system for unmanned aerial vehicles, or UAVs.
The “compromise system” that Amazon’s engineers propose relies on an array of sensors to orient the drone based on the sun’s position in the sky, if need be. That’s in case the drone gets confused by, say, lightning or a muzzle flash. Cont'd.. .
Records 1 to 10 of 10
Featured Product

BitFlow Introduces 6th Generation Camera Link Frame Grabber: The Axion
BitFlow has offered a Camera Link frame grabbers for almost 15 years. This latest offering, our 6th generation combines the power of CoaXPress with the requirements of Camera Link 2.0. Enabling a single or two camera system to operate at up to 850 MB/S per camera, the Axion-CL family is the best choice for CL frame grabber. Like the Cyton-CXP frame grabber, the Axion-CL leverages features such as the new StreamSync system, a highly optimized DMA engine, and expanded I/O capabilities that provide unprecedented flexibility in routing. There are two options available; Axion 1xE & Axion 2xE.
The Axion 1xE is compatible with one base, medium, full or 80-bit camera offering PoCL, Power over Camera Link, on both connectors. The Axion 2xE is compatible with two base, medium, full or 80-bit cameras offering PoCL on both connectors for both cameras.
The Axion-CL is a culmination of the continuous improvements and updates BitFlow has made to Camera Link frame grabbers.